This is where slashing comes in. Using Ethereum as an example, we’ll look at what slashing is, how it works and the limits it can create. Zoom in on slashing.
What is slashing?
Slashing is a mechanism designed to protect blockchains operating with the Proof of Stake consensus. On the Ethereum network, slashing punishes the operators of nodes that fail to perform their tasks correctly.
Indeed, the nodes used to validate the conformity of transactions on Ethereum have 2 other missions: to make the cost of an attack against the network excessive for attackers and to prevent other validating nodes from acting maliciously.
Although slashing is implemented on the majority of Proof of Stake blockchains, such as Tezos, Cosmos and Polkadot, it is the developers who decide whether or not to add this mechanism.
How does slashing protect the Ethereum blockchain?
As mentioned above, slashing is a mechanism that penalizes network participants who engage in fraudulent or malicious actions against the network. Validators on Ethereum are a key network entity, as they help to secure the network by verifying transactions on the blockchain.
Before a user can become a validator on Ethereum, he or she must place 32 Ethers (ETH) as collateral, a practice known as staking. As a reward, each validator is periodically rewarded with ETH if he or she performs his or her tasks correctly. This mechanism generates income, encouraging validators to contribute to the network’s security.
However, some validators may not respect the rules or may make mistakes. This is where the slashing mechanism kicks in to punish them and prevent them from doing so again.
In concrete terms, if a validator is affected by slashing, part of the ETH he or she has placed in staking will be deducted and burned. Since this can represent a significant financial loss, the operators of slashing-affected nodes have no interest in acting maliciously towards the network.
Why is slashing applied?
In general, validators are penalized when they fail to comply with network rules. For example, nodes may be targeted for slashing if they are offline for too long or if they attempt to double-spend. As far as inactivity is concerned, slashing is not applied because of malicious intent but because it can lead to security and trust issues. Punishment is used to encourage active participation.
Let’s take the example of Alice, a validator on the Ethereum network since she staked 32 ETH and runs her node.
One day, she signs two different blocks at the same level, which is forbidden on the network. Other validators detect this double signature and report the fraud to the Ethereum blockchain. As a result, a portion of Alice’s ETH, say 1 ETH, is burned as punishment for her malicious behavior. In the future, Alice will know that she cannot cheat on the network.
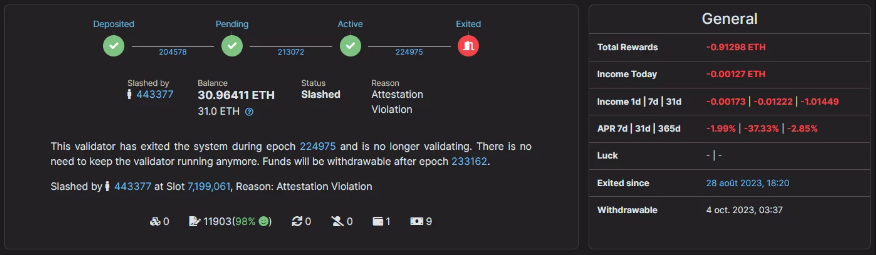
Since 2020 and up to the day of writing (September 2023), only 0.03% of validators on the Ethereum network have been affected by slashing, i.e., 279 out of 934,000 validators. This demonstrates the rarity and impressive effectiveness of this deterrent mechanism.
How can I avoid slashing?
First, before becoming a validator, the user must understand what slashing is and what the penalties are for those who break the rules.
Having acquired these basics, the validator must follow the rules, not cheat like Alice with double-spending, and maintain a reliable and active infrastructure to ensure that he doesn’t fail to validate.
Nevertheless, each protocol has its own rules when it comes to slashing. If you’re a validator on the Ethereum blockchain, the rules aren’t the same as with the Tezos blockchain.
What are the limits of slashing?
As you read this article, you may have already noticed some limitations of slashing.
In the first place, Alice probably unintentionally signed those two blocks, but in the end, she was punished by the network. Other validators regard human error and innocent or misinterpreted actions as an attempt to cheat.
Secondly, users are reluctant to operate a validator node, fearing falling victim to slashing and losing part of their ETH placed in staking.
Therefore, These limitations are not technical but psychological due to a certain reluctance from potential validators.
Conclusion
For the more fearful, there is a solution to guard against slashing: use protocols like Lido or Rocket Pool or centralized platforms like Binance rather than operating your nodes. Locking ETH via these protocols or platforms makes it possible to participate in Ethereum’s operation and receive interest through staking without risking being affected by slashing.
Moreover, using these protocols means that anyone can benefit from the advantages of staking on Ethereum without having to hold 32 ETH and maintain their node.
So there’s no need to manage an infrastructure and run the risk of being slashed. Professionals take care of it for you, and you’re paid in ETH according to your contribution.









